Writeup - QWERTY - HackDay 2022
Recover typed character from HID packet capture.
Subject
Flag is typed !
Challenge analysis
The file provided with this challenge is a packet capture file (.pcap).
So we open it with Wireshark.
We can see that the captured packets’s protocol is USB.
From the title and the subject of the challenge, and the fact that we have to find a flag, we can assume that this capture is from a QWERTY keyboard.
First we have to extract the captured data to be able to process them in an automated way.
For this we can use tshark:
tshark -r qwerty.pcap -T fields -e usb.capdata > qwerty.data
With this documentation we can see that keyboard captures are encoded on 8 bytes as follows:
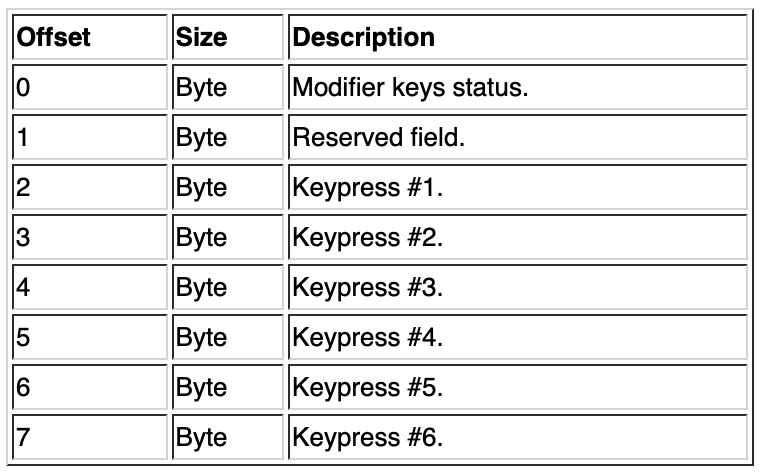
The first byte is encoded as follows:
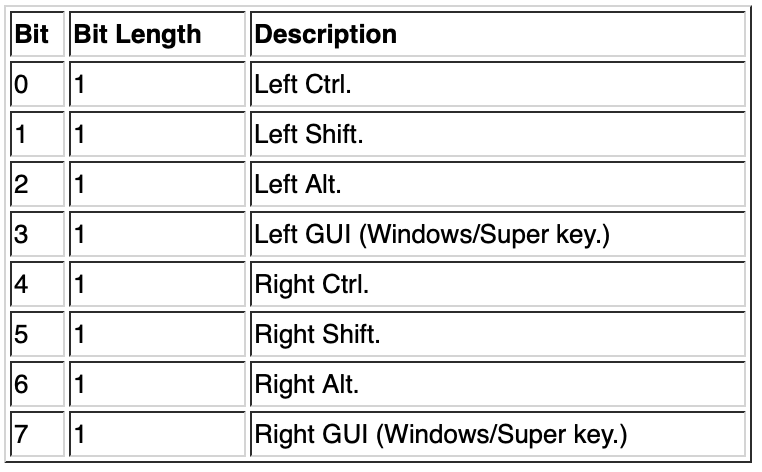
If the SHIFT key (left or right) is pressed, the first byte will be set to 0x02 or 0x20.
The second byte is always set to 0x00.
For the correspondence of the pressed keys (next 6 bytes), you can refer to the HID usage table.
It should be taken into account that CAPS LOCK only has an effect on letters, and that if it is activated and the SHIFT key is pressed, the letters will be in lower case again.
Decoding data
To automate the data decoding, you can find at here a script made for the occasion in Python.
Once the script is executed we can see the flag !
